Attack Recognition for Critical Infrastructure
Security Operation Center (SOC) as a service for the protection of KRITIS (CRITical InfraStructures) against cybercrime.
To protect IT/OT infrastructure effectively against cybercrime, hardware alone is not enough. It needs additional, highly specialized personnel to get this complex matter under control. And many smaller and medium-sized KRITIS operators do not have enough of them. This gap can be filled by external Security Operation Centers that provide an economic alternative to employing additional staff. An explanation from René Odermann, Account Director Development Cyber Security at Telent.
Theft, industrial espionage or sabotage: It is no longer a question of if a company will be the victim of a cyberattack, but when. 46 percent of German companies on the Statista business data platform that were questioned had experienced at least one cyberattack during the past year. The resulting costs for the whole of industry amounted to more than 202 billion Euros. The danger potential will rise in the future too – not least because of the geopolitical conflicts. To prevent security risks, to discover them, to evaluate them, to carry out checks and in the worst case to initiate a forensic analysis are the main tasks of a Security Operation Center (SOC). It combines technical tools, structured processes as well as experienced experts, and is comparable with a command center in which all the aspects of security within a company come together.
IT-SiG 2.0 Adds Responsibilities for KRITIS Operators
The German government wants to increase IT security nationwide. The new IT security law (IT-SiG 2.0) therefore extends the definition of KRITIS to include the refuse disposal and armament industries as well as the operations that are commercially relevant because of their size, together with their most important suppliers. They are all obliged under IT-SiG 2.0 to better protect their IT/OT environment against cybercrime by 1 May 2023 by employing systems for attack detection that comply with the current state of technology, and to provide proof of their implementation to the BSI (Bundesamt für Sicherheit in der Informationstechnik – Federal Office for Information Security). The IT-SiG 2.0 is aimed equally at the IT and the operational technology (OT) because it controls processes – whether for the power supply, the water treatment or in other critical infrastructure – that could have an enormous effect on the supply and security of the general public if they failed or were manipulated. The progression of digitalization has opened the originally isolated OT ever more and brought it ever closer to the IT. That has created many opportunities for cyberattacks.
The IT-SiG 2.0 law gives KRITIS companies the freedom to select their own individual solution for attack detection. Meeting the criteria will be a system for intrusion detection (IDS) and intrusion prevention (IPS). IDS/IPS specialized on the OT will understand the language of the proprietary protocols of the systems and controls, and can recognize attacks as well as any incorrect configuration caused by human error. When a problem is suspected, it can raise an alarm or block unauthorized data packets. An extension of this are honeypots, which are virtual machines that are intentionally configured with loopholes to attract hackers and lead them up the wrong path. The IP addresses of intruders can be identified via the permanently monitored honeypots so they can be blocked for the whole system and information about the methods of the attackers can be gathered.
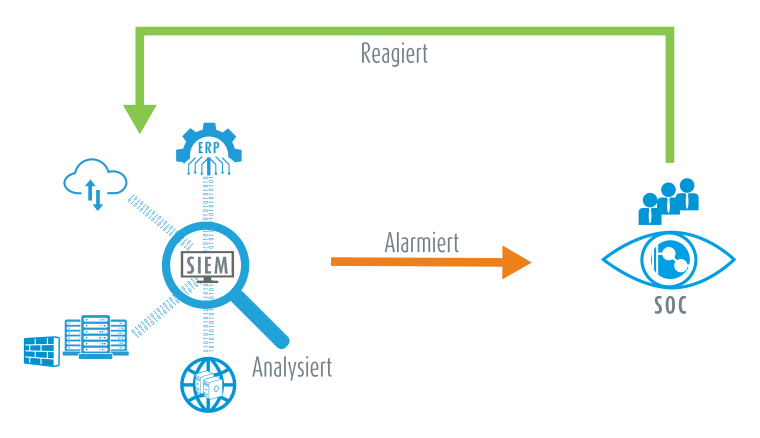
Real-Time Alerts Must Be Competently Evaluated
The three most important functions of attack detection are recording, detection and reaction. An important tool for the team in an SOC is a SIEM. The abbreviation stands for Security Incident and Event Management and describes a system that collects and aggregates reports, log files and numerous other data from relevant areas of the IT/OT infrastructure and highlights anything unusual. The data delivered must be evaluated and competently studied, with a view to the operational infrastructure, such as the active software versions, in order to react properly to an alarm. In practice, false alarms arise often. But who can handle this task? It just adds to the problems of many companies who are facing the challenge of limited personnel and skilled resources; to implement IT-SiG 2.0 they will have to jump even higher hurdles. Instead of building up internal capacity, which is no simple matter considering the dearth of available cybersecurity specialists, external providers of Managed Security Services are offering an alternative.
Companies can only achieve the ideal level of protection with the help of external service providers if they have the right specialists on board. This is not just about having the correct paper qualifications: Especially for complex IT/OT environments, their experience must also be appropriate, such as that acquired by Telent through its long-standing experience in industrial security and industrial automation for KRITIS operators, industrial companies and the public sector. For Telent, this means that all the legal requirements must be considered in detail for their ‘must, should and can’ criteria in order to firmly establish what can be provided as a service. Comprehensive understanding is a pre-condition to be able to implement technically valuable and reliable IT and OT security strategies within a holistic cybersecurity plan.
The focus is above all on transferring technology into a sensible service for every individual customer. The Telent team applies its deep-seated understanding of OT to find unusually versatile solutions, such as incorporating a company’s existing OT risk detection systems into the services of the SOC. As an experienced provider of managed security services, Telent monitors the networks of its customers around the clock, actively looks for threats, removes them and recommends further steps. In this way, the external SOC not only fills the personnel gaps but also strengthens cyber defense without companies having to make significant investments themselves in security software, hardware, security experts, training and everything else that is required to build their own SOC.
Author: René Odermann, Account Director Development Cyber Security at Telent










