Manage Security Effectively: G-SIM Security Information Management System from Geutebruck
Created as part of a mammoth customer project - G-SIM has meantime become the new Security Information Management System from Geutebruck. Conceived for medium to highly complex, ne...

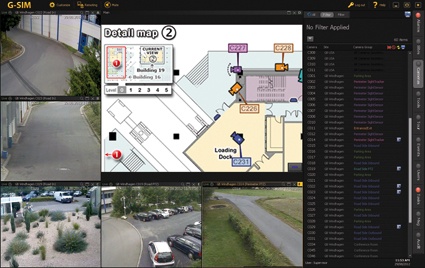
Created as part of a mammoth customer project - G-SIM has meantime become the new Security Information Management System from Geutebruck. Conceived for medium to highly complex, networked video security solutions, it provides seamless integration into the manufacturer's system world. The core functions are central user management, the simple management and operation using map-based control elements as well as the central recording of all relevant operational and system events. Matthias Erler of GIT-SECURITY.com spoke with Katharina Geutebrueck and Christoph Hoffmann, both directors of Geutebruck.
GIT-SECURITY.com: Mrs. Geutebrueck, the development of your new G-SIM Security Information Management System was a mammoth project that came about a part of a customer solution - with more than 400 recorders, around 6,000 cameras and 150 locations. Could you give us an overview of when you started, how many developers were employed and what level of investment was involved in the project?
Katharina Geutebrueck: You‘re quite right, it really was a very extensive project we undertook in Australia in response to a customer request. We started back in 2008 - since then it has become a completely new product for our customers. Back then we had some external partners, amongst others, an office of seven developers who were working to our specifications. We have invested some three million Euros into the development of G-SIM because it quickly became clear to us that we had here the opportunity to develop a wholly new security information system.
What else was necessary to bring the system up to series production level?
Christoph Hoffmann: After the project was completed, we decided to include it in our portfolio. We saw very clearly that the numerous features that were now technically mature could provide significant added value for customers in the market.
Katharina Geutebrueck: Our philosophy is generally to provide complete solutions. There was enormous potential available here, in particular because the solution we had at that time needed updating anyway.
Christoph Hoffmann: As our projects come in all sizes, a whole sequence of steps were necessary to make the product ready for our purposes and ready for market. That included first of all modularization - which enables us to offer not only complex total solutions but also individual packages. It was also important to have an understandable licensing model as well as menus and documentation translated into all relevant languages. Besides that we also developed comprehensive internal and external training courses.
What are the major characteristics of the solution? And what features do you hope will score most points with users, compared to competitors' systems?
Christoph Hoffmann: When we develop new products we always try to see things from the end user's perspective - and certain features are the deciding factors for him. These fall into five categories: ease of use, efficient alarm management, support for multi-user teamwork, centralized administration and the subject of redundancy.
Then let‘s start with the ease of use. What are the features here?
Christoph Hoffman: Above all we should mention here the interactive maps which make up the intuitive user interface. Creating a graphic site plan is extremely simple for the end user - and all formats and plans, as well as CAD drawings, can be imported. The information they contain is now dynamic, which helps particularly with larger projects where there are multiple system users. If an alarm is raised, it is shown on these site plans and everyone can see who is dealing with this particular alarm. This avoids duplication of effort. It is easy to drag cameras from the site plan to the viewer whenever required. The structure of the user interface is very simple and when there is an alarm the user is offered processes which are clearly-defined and easy to complete. These could be a security guard tour, lists with action instructions, etc.
... which takes us right into alarm management.
Christoph Hoffmann: Right. When there is an alarm , the users are given specific instructions together with the corresponding site plans. And the right cameras are also activated. That is all very helpful in the light of the nervousness and tension that usually occurs in such situations. The ability to prioritize users is also important, and is often specified in many projects. This enables the supervisor to take over from any user at any time, for example, taking responsibility for an alarm or control of a dome camera. He has priority and can have exclusive control of the camera. Incidentally, all alarms and the way they are handled are automatically documented by the system and can be subsequently made available in a report in all the usual formats like Excel or PDF. This enables processes to be optimized, weak points recognized, and if necessary action plans to be re-worked and keeps the ‘compliance monitors‘happy.
Can other systems like access control be connected?
Christoph Hoffmann: G-SIM is an open platform to which other systems can be docked. That could be, for example, access control, perimeter protection, fire or intruder security systems. The interfaces are absolutely flexible and are also made available to external developers in a comprehensive SDK (Software Development Kit). All connected systems and elements can be combined either graphically or with camera images within G-SIM.
Katharina Geutebrueck: It is generally our policy to offer open systems, but at the same time complete solutions. We do this because we know that the more simplicity and efficiency required in the application design of highly complex systems, the better the system components have to be matched with each other - and in the end that means compete systems from a single source. It's precisely this ease of use which we want to provide for our customers and we‘ll be expanding this approach increasingly in the future. Our maxim for G-SIM is clear: "Just a few people can effectively manage complex systems".
Let‘s come back to the central features of G-SIM. You spoke about teamwork with multiple users?
Christoph Hoffmann: When multiple users work with the system, each of them can see where the other is, which cameras and which site plan he is using and what he is currently doing. Alarms can be either manually or automatically forwarded to another member of staff. If the central control room is not occupied for whatever reason, the alarm will be directly transmitted
to another location that is manned.
And all events are recorded in an audit trail?
Christoph Hoffmann: Yes. A central sabotage-resistant database automatically logs everything that happens in the system, including what settings have been made, when and by whom. Later, alarms can be recreated in their original form so that, for example, an examiner can see exactly what the operator saw or ... what he should have seen. This function makes it possible to optimize processes or to change them. Access to this function (as to other functions), can be restricted, maybe to the works council, the data protection officer or a special security officer. The legal requirements here are very different internationally.
That just leaves the subject of redundancy. There is an integrated redundancy solution, in addition to external security systems. What is the background to this and how does the solution work?
Christoph Hoffmann: Nowadays in the IP field this is a ‘must have‘ as far as servers and cameras are concerned. With G-SIM server redundancy means that the system itself on which the program is running can be configured with redundancy. Then if a server fails, G-SIM imperceptibly switches to using the replacement server. The downtime is less than a second and nothing changes for the user - he continues to work in the same environment as usual. In addition we have the redundancy of the network video recorder. If there are, for example, ten NVR servers with 32 IP cameras each, the images from 32 cameras would be lost and could neither be display nor recorded if one NVR servers went down. G-SIM provides two options for this scenario: either the remaining NVRs take over these cameras or a reserve NVR takes them all. Again for the user, totally transparently and imperceptibly. It is just a question of the security requirements and of the budget. Our range of products is suitablywide.
For which areas of application is the system primarily intended?
Christoph Hoffmann: It is suitable for medium-sized and also for extremely large systems thanks to its modular and flexible architecture. We see the main area of application where live images, alarm management and reporting are particularly important: these are users that actively work with the images they are receiving - and for that you need a video management system. The standard viewer that comes with all our recorders is not the optimum tool in this situation. The emphasis with G-SIM is on efficiently managing any number of recorders, no matter where they are actually situated.
most read


Integrated and Futureproof: Traka’s Next Chapter
Interview with Stefni Oliver on Traka’s Vision for the Future

Is Your Venue Ready for Martyn’s Law?
Martyn’s Law demands stronger security by 2027. Is your venue prepared to protect and respond?

Airbus Defence and Space: Security as a strategic pillar of Europe's defense capability
Airbus Defence and Space protects sites, technologies and employees with modern security and cyber solutions - strengthening Europe's resilience in uncertain times

Between War and Peace: Hybrid Attacks and Their Impact on Critical Infrastructure
FOCUS TOPIC GERMANY - Hybrid attacks and drones: Security risks for Germany, its companies and critical infrastructure.





