Providing One Intelligent Layer of Security Around Temporary Sites

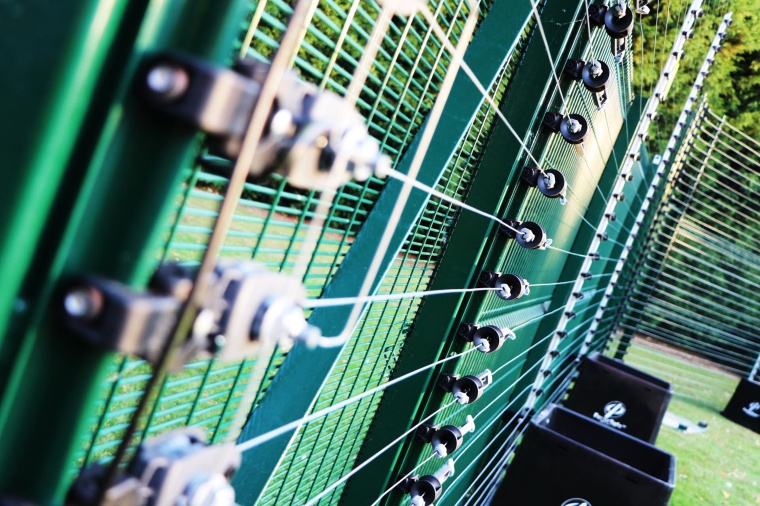

The evolving methods of terrorists, organized crime and opportunistic intruders have led to leaps in perimeter security technology, but the age-old principles still apply. Whether it‘s an ABC or Triple D approach, remember the basics, argues Richard Huison, general manager of Gallagher Security Europe.
The emergence of the vehicle as a weapon (VAW) as a deadly terrorist attack method has led high-security site operators to consider hostile vehicle mitigation measures to avert against vehicle-borne attacks. The obvious preference is to send all traffic through a single funnel. But customer experience and staff ease may demand a multi-funnel solution with its consequent challenge of cost, staff and risk management.
Site operators are therefore looking to harden their perimeter security with automatic bollards, barriers or turnstiles, speed gates and automatic number plate recognition systems. This ensures that only authorized personnel are on site. Cameras may also help at the perimeter, and an increasing use of drone technology and sophisticated object-recognition motion-detection algorithms to identify suspicious behaviors and send alerts to security guards can be noticed.
Appropriate for the Job
Sadly, VAW isn‘t the only threat. As the Manchester Arena bombing at an Ariana Grande concert in May 2017 illustrated, events where thousands of fans gather, all with their smart phones, and lots of international media present, represent a ‚terrorist playground‘ where global publicity for their cause can be gained. Here, permanent installations may be neither appropriate nor effective in protecting high-value temporary works. Precisely to offer a solution to this threat, especially around the highest risk or most vulnerable sites, we‘ve introduced a zero ground strike temporary host and PID fencing system with CLD Fencing Systems.
The Fence Safe-E rapid deployment system offers the classic three-fold perimeter protection of Defend, Detect and Deter in a viable temporary solution. While a physical fence provides defense and deterrent, it offers no detection. Video with complex analytics is great at detecting but doesn‘t provide any deterrent. The Fence Safe-E, with Gallagher‘s monitored pulse fencing (MPF), offers all three Ds in one solution. Even without delivering a shock on attack, an intruder‘s mindset on seeing the MPF, with warning signs that are required by law every 10m, is to avoid an attempt at breaking in.
Whatever physical and electronic solutions you opt for – from physical perimeter fencing and MPFs, gates, barriers, bollards and blockers, electronics such as PIDs, CCTV, video analytics, access control and even biometrics and mobile credentials – it is best to link them via a single control hub like our Command Center. It can receive and control, then analyze and report on threats, attacks and exceptions, sending bespoke images or instructions to mobile security patrols to achieve the smartest and most efficient perimeter protection.
Conduct the Usual Security Risk Assessment
Personally, I favor what‘s often referred to as the ABC model here. This considers the Area, Boundary and Contents. I recommend an increasing level of security the closer an intruder is to the most critical and sensitive assets. The perimeter serves as the first ‚cordon of security‘ in these successive levels of protection, though some now argue that, given the increasing power and definition of radar and CCTV, you could even establish security layers outside of the perimeter.
This principle was perfectly, but tragically illustrated by the story of former England one-day cricket captain Adam Hollioake, who remained in the International Cricket Stadium in Kabul, where he was working as a coach, while a bomb blast killed at least three people. Hollioake explained their protocol included three stages of security. Attackers had to breach the first stage, which was 100m from the ground, then the second, roughly 50m from the stadium, and finally only 15m away. In this episode, the man involved was caught at the first checkpoint and, on being apprehended, detonated his device and killed at least three of the security team and members of the public. So, I design from the perimeter inwards towards the center, taking each successive boundary as an opportunity to harden the security to thwart an intruder and enable security personnel to respond to any attempted security breach.
The Physical and the Virtual Threats
And remember that perimeter protection isn‘t simply about securing infrastructure or data. Done well, it should be about appropriate risk management against both cyber and terrorist attack as well as more traditional threats and, in turn, actually realize an opportunity for the host business to improve customer service, increase business efficiency and reduce costs. People, first and foremost, should be at the heart of the process in terms of the safety and security of premises and resources and also when it comes to planning and decision-making on appropriate protection measures.
For instance, the impact of any infection at a London desalination plant that produces 150 million liters of water per day would make the death toll at 9/11 appear totally insignificant. The next key point of potential vulnerability is at building access points. Too many facilities are still using standard key fobs and access cards as their electronic access control solution. Sure, there are cutting edge and somewhat costly solutions that use thumb prints or retina scans to track staff or visitors while on site.
Trusted Identity
Alternatively, you could consider upgrading to a solution that uses a mobile app for access control. After all, people very rarely lose their mobile phones – and they dare not even put them down any more. Such a system can set in motion an arsenal of recording and monitoring systems that are controlled and tracked by security managers. This is one of a number of ‚trusted identities‘ that I see increasingly in healthcare, government and finance and other sectors with a strong focus on regulatory compliance. Other ‚smart device‘ options include embedded chips and wearables. Critical national infrastructure may even benefit from biometrics to restrict access both to physical areas and to intellectual property.
Such systems recognize authorized personnel‘s unique ‚print‘ – such as their fingerprint, facial characteristics, voice or iris – to verify them, sometimes combined with another form of identification for double security. And AI technology such as Light Detecting and Ranging (LiDAR) potentially offers some ideas for improving security and safety in the future. It uses the pulse from a laser to collect measurements to create 3D models and maps of objects and environments.
Author
Richard Huison is general manager of Gallagher Security (Europe), whose customers include a wide selection of major European utilities companies. The largest is in the UK, which is also their biggest client worldwide for perimeter protection, covering 700 sites through different channel partners via the Gallagher Command Center at two Alarm Receiving Centers.
Business Partner
GallagherUnit 5, Eastboro Fields Hemdale Business Park
CV11 6GL Nuneaton
UK
most read


GIT SECURITY AWARD 2026 - The winners have been announced!
GIT SECURITY AWARD 2026: The best safety and security solutions of the year - now an overview of all winners

Assa Abloy's battery-powered Aperio KL100 secures lockers
Boost workplace security and operational flexibility by securing more than just doors.

Sargent & Greenleaf Joins the Assa Abloy Group
A new chapter of global growth for Sargent & Greenleaf opens with their integration into the Assa Abloy Group

Security management, building security & perimeter protection: the winners of category E at the GIT SECURITY AWARD 2026
GIT SECURITY AWARD 2026: Security management, building security & perimeter protection - an overview of the most innovative solutions




