Authentication: focus on security
With the right know-how, the development and implementation of a sustainable and secure au-thentication solution with RFID will be successful.

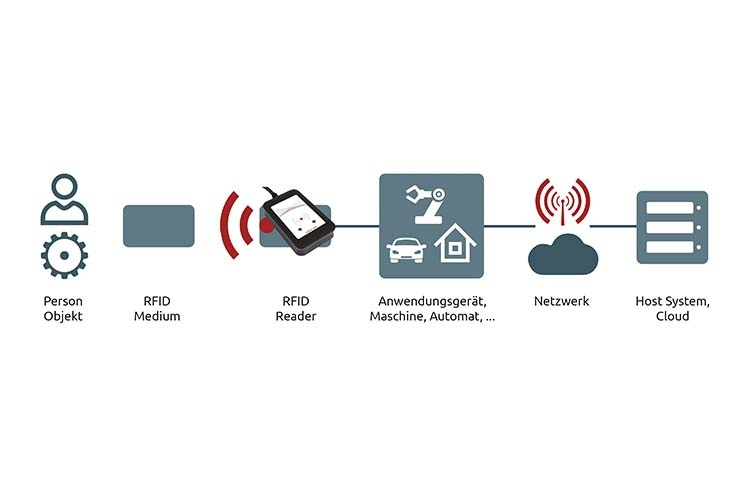
Whether it's access to the office or the use of an electric charging station, modern authentication and access control solutions make everyday life easier. With the increasing use of RFID for object and person identification, the requirements for data security are growing. This is because automated programs can be used to identify and track an object or person and record, store or transmit sensitive information about their activities or movements. Legislators are therefore imposing strict requirements specifically for the protection of personal data.
For years, there have been controversial security discussions when it comes to data collection and storage. Against this background, data security is the top issue for every company security officer when implementing an authentication solution.
How can companies future-proof their security strategy for authentication solutions?
- Observe legal requirements and regulations.
- Understand protection goals related to data security and consider them as part of the security strategy.
- Identify real or potential threat scenarios and make them the basis of the protection concept.
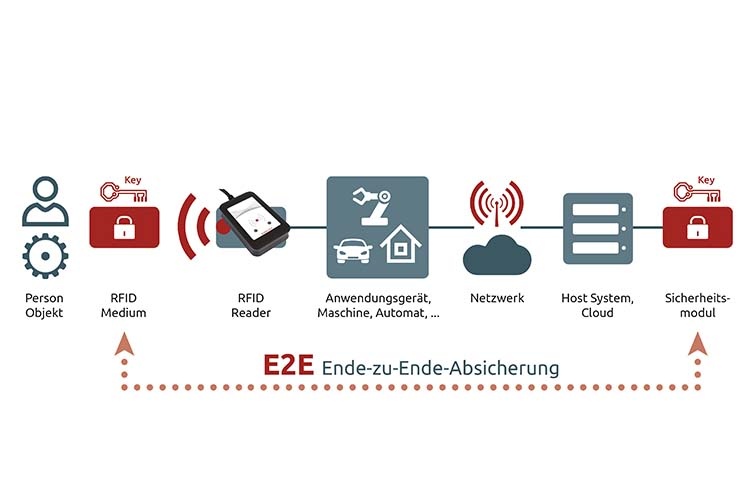
- Always consider safety in relation to the overall system. Overall safety is only as good as the weakest link in the chain.
- Effectively secure authentication systems with cryptographic methods.
Security officers should act with foresight. Elatec's whitepaper provides detailed answers to all questions about implementing a secure and efficient authentication solution.

most read

Security management, building security & perimeter protection: the winners of category E at the GIT SECURITY AWARD 2026
GIT SECURITY AWARD 2026: Security management, building security & perimeter protection - an overview of the most innovative solutions

Intersec 2026 Reinforces UAE’s Leadership in Global Fire Protection and Emergency Response
Intersec taking place from 12–14 January 2026 set to welcome over 1,400 exhibitors

Sargent & Greenleaf Joins the Assa Abloy Group
A new chapter of global growth for Sargent & Greenleaf opens with their integration into the Assa Abloy Group

Safety and Security in an Emergency: How companies take responsibility with strategic personal protection and amok prevention
Personal protection & amok prevention: strategic concepts, training & responsibility for corporate safety and security

Airbus Defence and Space: Security as a strategic pillar of Europe's defense capability
Airbus Defence and Space protects sites, technologies and employees with modern security and cyber solutions - strengthening Europe's resilience in uncertain times






