How Reliable are Electronic Access Control Systems?
Electronic or digital access control opens a lot of opportunities. But how can you protect yourself against manipulation? We interviewed industry experts Axel Schmidt and Werner St...



Electronic or digital access control opens a lot of opportunities. But how can you protect yourself against manipulation? We interviewed industry experts Axel Schmidt and Werner Störmer from BHE, the German Association of Security Systems Manufacturers and Installers to get tips for installers, integrators, operators and end customers. Our scientific editor Heiner Jerofsky spoke to graduate industrial engineer Axel Schmidt and industrial engineer, technical author and advisor Werner Störmer. They are respectively the chairman and the deputy chairman of the specialist access control committee at BHE. They talk about new trends, security, hacking, mechatronics, biometrics and a wide range of security levels for access control technology.
GIT SECURITY: Axel Schmidt, where do you see the most important benefits and opportunities to use mechatronic locking systems?
Axel Schmidt: The differentiation between mechatronic locking and offline/online systems is almost a thing of the past. These days the lines are usually blurred. The mechatronic locking system is one part - and usually an extremely large component - in the access control system. With mainly battery-powered components (locks, cylinders, padlocks etc.), parts of buildings can be reached, which could not be mapped cost-effectively with conventional online access control systems. This applies mainly to doors, but also cabinets, furniture, lockers, etc. The life cycle costs of offline access control systems are lower compared to mechanical locking systems, combined with a disproportionate increase in security and flexibility.
Access control systems are used in a wide range of offline and online systems. Can you explain the differences, function and use, as well as the advantages and disadvantages?
Werner Störmer: Depending on the level of security and conditions at an access point, both autonomous and online access control systems are available. Autonomous terminals or mechatronic locking systems operate independently, without a connection to a higher level access control center and are each responsible for a single access point. The advantage is the low installation cost, however, there is usually no possibility of transmitting the door status and alarm messages (e.g. unauthorized access attempts) to a control center. Their benefits, use and possible integration into networked access control systems have already been explained by Axel Schmidt. Networked systems with a higher level access control center, to which separate pass or biometric reading devices or access control systems/separation devices can be connected, are more user-friendly and can be put to a wider range of uses. What should be noted are the possible number and type of network connections (e.g. star or bus-type connection, by radio or cable) for the access control devices that need to be connected. In addition, the following features are worth mentioning:
- Rapid blocking of lost cards
- Convenient input, processing and editing of saved access and authorization data
- Cross-area functions, such as route monitoring or automatic control from a central point
- Possible integration of other IT or card-controlled applications
If certain software functions and checks are allocated in the access control system or access control terminal, increased security can be achieved, by means of an additional emergency power supply. If the access control server fails or cable break(s) occur, the access control system or access control terminal continues to operate autonomously until all the system components are functional again.
There is a tendency to link time and access control systems, together with vehicle access control and visitor management. To save costs, it may be advisable to use the same network, pass and identification systems and possibly even the same terminal. With a single logging process, the time when an employee begins work can be recorded and access can be authorized. A further advantage is that the same master data can be used with the entry and access authorizations of the employee. Networked access control systems usually form part of an integrated security concept with intruder alarm systems, video surveillance and central control. This also includes the integration and control of separation devices, such as turnstiles, access locks and barriers.
Radio-networked, Cloud and smartphone-based, or mobile access control systems are becoming increasingly available. What are the advantages and disadvantages compared to conventional networked access control systems?
Axel Schmidt: A major disadvantage of offline access control system components is precisely that they are offline and have no connection with the host system. To alleviate this disadvantage, over the past decade, virtual networks have been developed, in which information is distributed and collected using means of identification, according to the snowball principle. The ball started rolling with the development of battery powered radio technology solutions. Smartphones have become an essential part of our lives and BLE (Bluetooth Low Energy) provides a standard, which can be widely used for access control. The development of online access control is also moving away from the old models and browser-compatible systems towards Cloud-based solutions. For many years now, the major software companies (Microsoft, SAP, DATEV, etc.) have shown that the future lies in Cloud-based software. Access control is a part of digitalization. This will result in more users, more data, greater flexibility and increased security.
Smartphones are becoming increasingly popular when it comes to access control solutions. How do you see developments in terms of local conditions, user mentality and legal aspects?
Axel Schmidt: These developments are both opportunities and risks. The opportunity is a continuously available medium with online function, which always has almost all technologies on board, including BLE, NFC and HCE. I consider the main risk to be inadequate protection against manipulation, hacking, data theft, etc., especially with unqualified developments and products. It must be possible for users to clearly identify whether products are professional security technology or unreliable Smart Home technology.
Werner Störmer: From my point of view, although the possibilities of using smartphones in and for access control are very promising, they are not suitable for all companies, areas of use or groups of users. For example, carrying smartphones is prohibited in medical facilities and departments where there is a risk of espionage. Legal aspects, such as the handling of personal data and co-determination regulations, must also be considered. There is hardly any way of influencing what a user saves on his smartphone and how he uses it. I consider the BLE standard to be especially critical, as it enables hackers to obtain access via the radio connection and possibly take control of the device. Within a radius of up to 10 m, there is also the danger that an authorized person unlocks one or more secured doors with their smartphone using BLE, so that unauthorized persons can pass through them. In my opinion, due to the effort and expense involved in making the change, companies will continue to use tried and tested passes. The best example of this is the magnetic strip, which has been used for money transactions since 1950. In spite of technologies, such as chips, NFC and BLE with smartphones, it will be a long time before we arrive at a comprehensive solution.
What about the security of networked systems? How great is the risk of hacking?
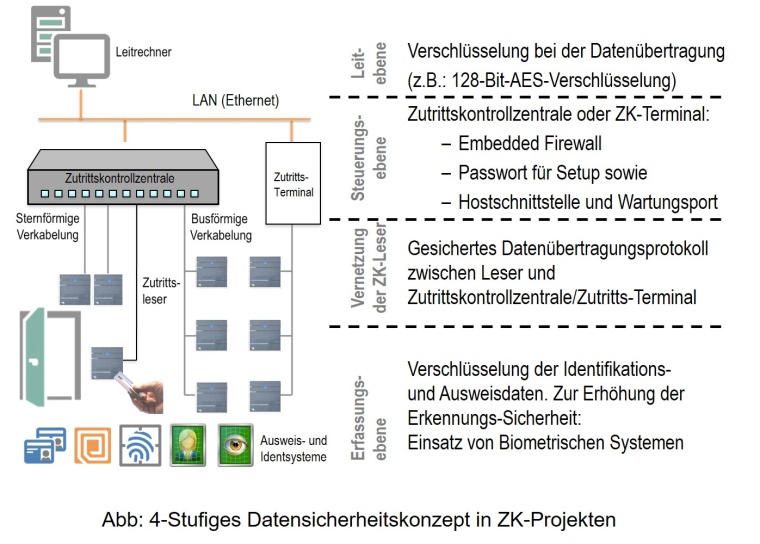
Werner Störmer: Mechanical, software, structural, electronic and personal security measures are necessary, in order to protect the weak points of an access control system, while also ensuring high system availability. System crashes or faults, e.g. due to failure to comply with installation instructions, critical ambient conditions, power failures or quality defects in the components that are used are more probable than the risk of encrypted connections being hacked. In order to protect the transferred data against manipulation or hacking, encryption can be carried out at various levels, from with identification (ID) and data transfer to control and application level.
- At recording level: ID carrier (pass/biometric feature) and exchange of data with an access control reader
- For transfer via the data lines: between the recording level (ID system/access control reader/access control terminal) and access control center, as well as in the LAN between the access control center and application server.
- For a defined, closed group of users.
A four-level hierarchical password concept can ensure that any personal data that is recorded remains confidential. At the lowest level, the in-house technician can configure the communication protocol or set the IP addresses for the Ethernet connection using his password. A supervisor can allocate additional passwords, specify maintenance groups or change parameters in the access control terminal. The system administrator at the highest security level is, for example, the only person that can change encryptions and activate the firewall in the terminal or access manager. Secure access control can only be ensured if there are no weak points in the specified security chain.
Do we need to worry about smart homes?
Axel Schmidt and Werner Störmer: Smart products offer greater comfort and more efficient use of energy. Many suppliers wish to keep up with trends and use attractive adverts to flood the market with countless, reasonably priced smart home products. But caution: With these products, which are intended for DIY installation and can be purchased online for a few Euros or from your local DIY store, we need to consider a few points. They rarely meet security quality criteria and are not usually installed and used “correctly”. They also claim to provide people with total security, which certainly cannot be achieved with these systems. For customers, the differences between high quality security technology and cheap products are difficult to identify. Consumers who want their homes not only to be “smart” but also protected against burglary and smoke should consult a qualified specialist security company. They are familiar with the relevant regulations, know which aspects need to be considered and use professional security systems. Several points must be considered, if the systems are to run smoothly and provide reliable protection.
What do the differences in security level and classification mean for the use of access control solutions? What do users need to know?
Axel Schmidt: The current EN 60839-11-1 contains four risk levels. The categorization is made by the operator according to his security and organization requirements, as well as a previous risk assessment conducted, if necessary, with the supplier. The risk assessment is not the subject of the standard, but it does provide relevant instructions. Annex A of the standard is also crucial, as it lists the requirements for the 4 security levels, which do not necessarily need to be met in every system that is installed, if this is not required by the operator. However, the systems that are used must be able to meet the requirements, which depend on security levels. In practice, this view results in access control systems that include several or all security levels. The standards only cover the access control system with its interfaces to the access point, users, operators and other (alarm) systems. Other standards apply for the other mechanical components.
In mid-2017, a critical article in a German security magazine claimed that it is technically possible to open any lock. What do you think about this idea? How well are electronic access control systems protected against manipulation?
Axel Schmidt: The article showed our industry in a very negative light and was not very helpful, but rather discouraging for users, planners or installers. According to these statements, almost all access control systems with online access must be insecure. That is nonsense.
Werner Störmer: It is a truism that with sufficient effort, almost any type of lock can be opened. There really is no such thing as absolute security. The amount of criminal energy needed to open or break through an access point always depends on the level of security that is implemented. In a hotel, I know that employees can enter my room and, in an emergency, they can also open the room safe, so I act accordingly. It is just the same in a company. A baker’s shop can be secured more easily than a bank. If a lock or a door is opened without authorization, the networked online door monitor should trigger an alarm. In addition, for access control, not only “door locks” are used but also, for example, separation devices with video surveillance. Careful planning and sound technical knowledge on the part of the installer ensure that sabotage, manipulation and unauthorized access are largely excluded. Starting with personal identification from secure identification procedures and/or biometric features and encrypted data transfer at all levels to an emergency power supply and suitable perimeter protection, the highest possible security level can be achieved.
How secure are the currently available identification and reading methods?
Werner Störmer: RFID technology has established itself in this field. It provides contactless identification (including without visual contact), protection against copying, encoding of information and multifunctional use (time, access, log-in, canteen, etc.), with the protection of applications amongst/against each other. The absence of reading apertures, such as those used for insertion or swiping procedures, also means that it can be used in dirty environments and reduces its susceptibility to faults and manipulation. The encryption technologies Mifare DESFire EV1/2 (AES-128) and Legic advant (DES/3DES) provide relatively high security.
What is the current status of developments and security against manipulation for biometric identification methods?
Werner Störmer: Biometric methods are intended to eliminate the weak points of other ID methods, such as “forgotten, lost or damaged passes”. At the moment, fingerprints, hand geometry, vein detection, iris and facial features are used as static methods for access control. When it is used for the first time, on “enrollment”, the key features of each participant are saved as reference data (template) and compared against the currently recorded measurement values, which are required as identification for access control. If these concur and access is authorized, access is enabled. The saved data record does not contain any “raw data”, such as a passport photo or fingerprint, but only features that are extracted from them, such as a mathematical description of the ends and branches of the fingerprint lines or the iris pattern in the case of iris detection. One of the most secure biometric technologies is hand vein recognition. In contrast to fingerprints, the vein pattern on the palm of your hand cannot be forged. If a latest generation RFID card for opening a separation system is combined with hand vein identification in the access lock, access can be secured so that unauthorized access can be almost completely excluded. Data protection problems are almost completely eliminated if the template is not saved centrally and users administer the pass as the storage medium for the biometric features. Central storage leads to the risk of misuse and potential damage, e.g. due to hacking. As passes are usually used for other card-controlled applications, if the security requirements are very high, the pass input can be combined with biometrical identification. For data protection reasons, the template can be saved on the RFID card.◾
most read

Assa Abloy's battery-powered Aperio KL100 secures lockers
Boost workplace security and operational flexibility by securing more than just doors.

Safety and Security in an Emergency: How companies take responsibility with strategic personal protection and amok prevention
Personal protection & amok prevention: strategic concepts, training & responsibility for corporate safety and security

GIT SECURITY AWARD 2026 - The winners have been announced!
GIT SECURITY AWARD 2026: The best safety and security solutions of the year - now an overview of all winners

Integrated and Futureproof: Traka’s Next Chapter
Interview with Stefni Oliver on Traka’s Vision for the Future

Airbus Defence and Space: Security as a strategic pillar of Europe's defense capability
Airbus Defence and Space protects sites, technologies and employees with modern security and cyber solutions - strengthening Europe's resilience in uncertain times




