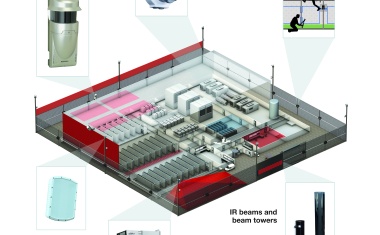
Security and Access Control Upgrade Programme for Replay’s Premises
With innovative flair, characteristic Italian design and the quality of its products, Replay has become a leader in jeans and denim based clothing manufacturers. Since 1996 Replay ...