Special Focus Access Control: The Ins And Outs
An Overview of Some of The Access Control Systems and Solutions Currently Available.









You can see details of new features and functions of access control systems in every issue of GIT SECURITY. The approach of each manufacturer to providing the best solution varies of course, and the result is a broad spectrum of products and services that cater for the wildly different needs of all the users, ranging from international mega-companies to the one-man-band business, from installations in the searing heat of the Middle East to the permafrost of Greenland, from the sea salt-bashed coastline of Cornwall to the mountain tops of the Alps. In short, there‘s a solution for every need. So we‘ve put together a brief summary of some of the systems that you might like to investigate further to cover your particular access control needs.
Let’s start small: there’s often a need to protect a small outbuilding, even a shed, that just has one door. Keeping a mechanical key somewhere else, or dangling on your personal key fob all the time when it’s only rarely used can be tiresome and inconvenient. Luckily, simple systems are on the market that just require either a PIN or your mobile phone to unlock the door. You might consider one of the solutions from Abus here – simply swapping out the lock cylinder with one from their wAppLoxx or CodeLoxx range already brings you into the world of secure electronic access control, while their SLT demands a PIN before opening the door for you. Alternatively, the components of the XS4 system from Salto together form a tailor-made, wire-free solution to fit almost any door. The system is also scalable – read ‘expandable’ – to grow with your needs.
If you’re still not quite ready to give up the traditional key, then the Cliq system from Assa Abloy could be interesting for you. Along with electromechanical lock cylinders, the range also includes weather-protected padlocks for objects like gates or sheds that require that sort of locking. Centralized administration with traceability from the event log enables authorized administrators to track which keys have opened which doors. A similar concept is offered by Winkhaus with their blueSmart system. The components of this cable-free system communicate with one another to process and distribute access authorizations very quickly.
Out in the Field
Utility companies face a pretty unique problem in that they have a lot of expensive – and critical – infrastructure distributed all over the towns and the countryside. Electricity sub-stations are one example, water pumping installations are another. Rather than having dozens of individual mechanical locks with personnel having to carry a unique key for each with them, the clever solution these days is to install electronic locks that recognize a token, like key fob, a card or even a mobile phone, for example. Just one physical device is then required to access all the infrastructure installations for which that person is authorized. Maintaining control of who is allowed where and when becomes an extremely easy task for the administrator, and there’s no need to cut keys or change locks if one gets lost. If this scenario applies to you, then you might consider the MobileKey solution from SimonsVoss to make your security administration a lot easier.
The Busy Office
The daily peak of hundreds of employees coming through the turnstile almost at the same time could cause some access systems to break into a sweat. A well thought out system, however, will not only cope with the rush but also provide value-added data in the process. In an emergency for example, the access control system already knows who is on site and can instantly provide a list of people to be accounted for in a roll-call. Tyco has a range of systems that can be configured to suit the size and security level of your organization, from small and simple items from their Kantech range right up to mission-critical control and customized CEM Systems and Innometriks solutions.
Even the devices at specially restricted areas that require multiple accreditation or biometric data to enter will deliver valuable data should the theft of data, designs or other intellectual property be discovered later. And in less critical areas, it is still essential to stop just anyone from wandering through offices and sites, so employees will appreciate the convenience of carrying a small fob or a card that will grant them immediate access to places that they need to be. This will ensure not only their personal safety and the security of their possessions, but also that of the company. A whole palette of products from Deister Electronic can provide a new access control system based around their manufacturer-independent Cipher Card, or upgrade an existing one to instantly provide more convenience and higher a security level.
Come inside a building and there are dozens of other items to which access should be restricted, such as medicine cabinets, retail display cases holding valuable items, or even the cabinets housing your own IT infrastructure. Senseon have put together a very useful website to help you make decisions and choose the right system. Their cabinet access control systems and electronic locks will find many uses in securing furniture and fittings throughout many different user groups, such as healthcare, high-end retail and hospitality locations, but also in a domestic environment.
Out and About
Of course, it’s not only doors that have access control; turnstiles and gates can equally well be integrated into a comprehensive system that covers the entire site, including people access to fenced-in areas such as outside parking or storage areas. To effectively regulate people and vehicle access, you will find a wide range of tested and certified solutions, such as barriers, sliding or folding gates, bollards and road blockers, available from PPG (the Perimeter Protection Group). The Aeos system from Nedap can look after these installations as part of overall site security and bring many other useful features with it, such as identity management, badge printing, and biometric data enrollment. The data generated by the system helps to analyze people flow and staff movement.
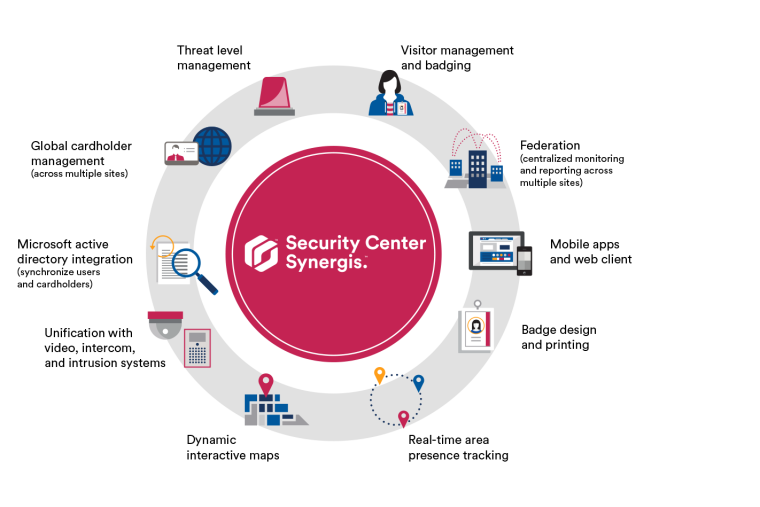
No matter what you’re restricting access to, be it expensive jewels, intellectual property, sensitive data or materials, it can be very advantageous for your security team to have some interaction between security systems. Genetec offers the IP-based Synergis Security Center that also incorporates these endangered locations into the overall security picture, even those equipped by third-party suppliers. This integration of access control equipment and the unification of other security systems brings some very convenient benefits, such as providing a single intuitive interface for otherwise disparate systems, automating vehicle access or generally lightening operator workload through the intelligent application of video analytics.
One Human Interface
The access control software packages offered by Bosch Security to meet needs of varying complexity also achieve this. Their APE, AMS and BIS-ACE solutions all support the OSDPv2 secure protocol between system elements and can integrate third-party functions such as Human Resource systems and, for the BIS-ACE, building automation products. In a similar way, the Win-PAK solutions from Honeywell provide scalable software that manages disparate systems through one interface, growing as additional security requirements are covered, even over multiple sites.
Of course, there are many other developers and suppliers of access control hardware and systems on the market worldwide. We hope the examples above give you at least a starting point to find the optimal solution for your particular needs. If you’re not successful, let us know and we’ll put you in touch with our heavyweight friends from the local boxing club who can provide a short-term, if somewhat unpredictable, access control service.
Contact
Abus – www.abus.com
Assa Abloy – www.assaabloyopeningsolutions.se
Bosch – www.boschsecurity.com
CEM – www.cemsys.com
Deister – www.deister.com
Genetec – www.genetec.com
Honeywell - www.security.honeywell.com
Nedap – www.nedapsecurity.com
PPG – www.perimeterprotection.net
Salto – www.saltosystems.com
Senseon – www.senseon.com
SimonsVoss – www.simons-voss.com
Tyco – www.tyco.com
Vanderbilt – www.vanderbiltindustries.com
Winkhaus – www.winkhaus.com
Read on: Three Questions for Three Mobile Access Experts
f.l.t.r. Thomas Schulz, Assa Abloy Opening Solutions EMEA; Vincent Dupart, STid; Michael Unger, Salto Systems
most read

Safety and Security in an Emergency: How companies take responsibility with strategic personal protection and amok prevention
Personal protection & amok prevention: strategic concepts, training & responsibility for corporate safety and security

Training at Fraunhofer SIT: Strengthening resilience against cyber attacks
Knowledge in cyber security is evolving rapidly - continuous training is therefore important.


Is Your Venue Ready for Martyn’s Law?
Martyn’s Law demands stronger security by 2027. Is your venue prepared to protect and respond?

When the Internet stumbles: Why DNS is important
When DNS fails, the internet stumbles-AWS outage proves resilience and redundancy are vital for digital trust









