Bosch Sicherheitssysteme: increasing effectiveness and reducing costs of CCTV-based security systems – Part I
Bosch Sicherheitssysteme: increasing effectiveness and reducing costs of CCTV-based security systems - Part I. In the first part of this article, Ruud Toonders looks at how simple ...

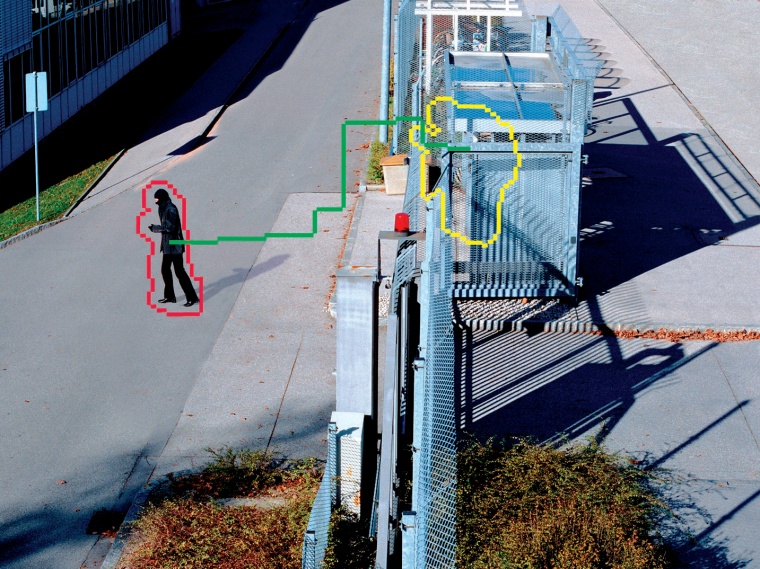
Bosch Sicherheitssysteme: increasing effectiveness and reducing costs of CCTV-based security systems - Part I. In the first part of this article, Ruud Toonders looks at how simple video surveillance has developed from watching banks of monitors to sophisticated computerised scene analysis, and how abnormal situations are now automatically recognised. Applying the latest technology can simplify operation and ease the strain on security personnel.
Smart surveillance is not new. Essentially it involves digitally analyzing the signal from a CCTV camera using smart Video Content Analysis (VCA) algorithms capable of identifying and marking specific features in the video content that may require action. But the algorithms nowadays are getting much smarter and have come a long way from the relatively simple Video Motion Detection (VMD) algorithms of a few years ago.
VCA compares real-time video with ‘known rules’ for detecting alarm situations or suspicious activity. Today’s VCA algorithms deployed in the more advanced video security solutions are capable not only of motion detection, but also of detecting specific objects like abandoned baggage, direction of movement and even suspicious behavior such as loitering – all in real time. These systems also operate 24/7, are never distracted or bored and never have an off-day – in contrast to their human counterparts.
Moreover, they are clever enough to spot patterns of behavior that may pass unnoticed by even the most vigilant human operator. VCA-enabled systems can also easily be configured to trigger a recording only when events that violate the ‘known rules’ are detected, dramatically reducing the amount of recording disk capacity required. What’s more, today’s smart surveillance systems can significantly cut costs by reducing the number of security personnel needed to monitor the video, and allowing them to concentrate exclusively on incidents that require human intervention or decision making.
The All-seeing Eyes
The latest VCA algorithms utilize the increased processing power and intelligence inherent in today’s digital video security products. One of the most advanced is the new Intelligent Video Motion Detection (IVMD) algorithm currently deployed by Bosch Security Systems in its IP (Internet Protocol) network video products. The functionality offered by this algorithm is typical of what users can expect to find in top VCA products marketed by leading security-system manufacturers such as Bosch.
Changes in environmental conditions are one of the major causes of false alarms in VCA systems. To eliminate this, the IVMD functionality includes an advanced background-learning algorithm that suppresses unwanted notification from, for example, moving tree branches, leaves, clouds, shadows and falling rain and snow. The algorithm is also capable of dynamically adapting to changes in background so that alarms are triggered only in real alarm situations.
These advanced VCA algorithms also allow the user to create independent detector fields with individual alarm trigger parameters. Even completely overlapping or identical shapes with different trigger parameters can be set. In the case of Bosch’s IVMD 1.0, alarm parameters such as size, speed and direction discrimination can be set up independently for each of the detector fields, allowing, for example, a single camera to monitor an outside parking lot and detect whether cars are speeding or driving the wrong way.
It is also possible to calibrate the cameras to allow objects to be distinguished by their size. This calibration includes the addition of 3-D camera perspective correction necessary for reliable size and speed discrimination in all directions. With this funcfunction, alarms can be triggered only on objects below or above a specified size, for example just for trucks or cyclists, or just for objects travelling below a specified speed, such as a pedestrian walking along a highway.
Monitoring Suspicious Behaviour
It is difficult to precisely define what constitutes suspicious behavior. Often it’s a matter of experience and even intuition, as any long-serving police or security officer will attest to. But there are certain patterns of behavior that can be interpreted as potentially suspicious such as people moving in the opposite direction to the normal flow of traffic when approaching an airport security checkpoint, or continually returning to the same point for no apparent reason.
Advanced VCA algorithms can be set to trigger on such behavior. Upcoming versions of Bosch’s IVMD, for example, will be capable of discerning suspicious behavior based on the trajectory a moving object takes through the video even if it is momentarily obscured by other objects. So if a person is loitering around a particular area, he or she will create an uninterrupted trajectory and this can be set to alert security personnel.
In part 2 of this article that will appear in the next issue, we‘ll be looking more closely at some of the practical applications of VCA, video evaluation and object classification, metadata generation and at giving the system intelligence where it‘s needed.
Ruud Toonders
Contact:
Erika Görge
Bosch Sicherheitssysteme GmbH,
Ottobrunn, Germany
Tel.: +49 89 6290 1647
Fax: +49 89 6290 1193
emea.securitysystems@bosch.com
www.boschsecurity.com
most read

When the Internet stumbles: Why DNS is important
When DNS fails, the internet stumbles-AWS outage proves resilience and redundancy are vital for digital trust

Safety and Security in an Emergency: How companies take responsibility with strategic personal protection and amok prevention
Personal protection & amok prevention: strategic concepts, training & responsibility for corporate safety and security

Airbus Defence and Space: Security as a strategic pillar of Europe's defense capability
Airbus Defence and Space protects sites, technologies and employees with modern security and cyber solutions - strengthening Europe's resilience in uncertain times

Integrated and Futureproof: Traka’s Next Chapter
Interview with Stefni Oliver on Traka’s Vision for the Future

Training at Fraunhofer SIT: Strengthening resilience against cyber attacks
Knowledge in cyber security is evolving rapidly - continuous training is therefore important.









